Why Every Chapter Facility Needs an Evacuation Plan
This summer’s devastating floods in Texas and North Carolina are sobering reminders that severe weather can escalate quickly—sometimes in minutes. For sorority chapter facilities, where dozens of members may live, sleep, or gather under one roof, having a clear evacuation plan isn’t just a precaution—it’s a necessity.
Emergencies Don’t Wait
Whether it’s a flood, fire, hurricane, or another emergency, conditions can deteriorate rapidly, leaving little time to think, much less coordinate. That’s why preparation and practice are key. Every chapter facility should have an evacuation plan that is:
- Clear – Easy to understand, even under stress
- Accessible – Posted in common areas and shared with all residents
- Practical – Tailored to your facility’s unique layout, exits, and risks
- Reviewed and Practiced – At least once per semester, if not more frequently
Use Our Sample Plan to Get Started
To make it easier to take action, we’ve developed a Sample Evacuation Plan you can use as a template. It includes key roles and responsibilities (like who grabs the emergency binder), a meeting location, and tips for communicating during a crisis.
Keep in mind: a plan that just sits in a binder isn’t a plan that will protect your members. Practicing your evacuation procedure helps identify weak points and builds the muscle memory needed to respond calmly under pressure.
Who’s Responsible?
Whether you’re a chapter leader, house director, or local volunteer, you have a role in making sure your chapter is ready. Start the conversation now. Schedule a drill. Assign roles. Walk the exit routes. These small actions could make a life-saving difference.
We have more Emergency Planning resources in our website library.
Across the U.S., disaster-related losses have exceeded $1 trillion in just the past seven years—but it’s not only hurricanes or wildfires causing damage. More frequent threats like water leaks, power outages, and storm damage are becoming costly realities. For house corporation volunteers, the old approach—“buy insurance and react to loss”—is no longer sufficient. With insurers tightening terms and raising premiums, proactive risk hardening is now essential.
What Is “Risk Hardening?”
Risk hardening means taking proactive steps to make your chapter house stronger, safer, and better prepared to handle damage from things like storms, water leaks, or power outages.
It’s about investing in simple upgrades, preventive maintenance, and smart planning to reduce the chances of serious damage—and to help your facility bounce back quickly if something does go wrong.
For example, installing leak detection sensors, reinforcing the roof, trimming back trees, or creating a basic emergency plan are all ways to “harden” your risk.
Think of it as safeguarding the chapter house now to avoid bigger problems later.
Why You Should Care
Taking preventive steps can significantly reduce both financial and operational impact for chapter houses. Every $1 spent on mitigation saves roughly $4–6 in post-disaster recovery costs. That’s savings you can invest back into your facility and protect your members’ well-being.
Smart Risk Hardening Measures
| Area | What to Do | Resource |
|---|---|---|
| Leak Detection | Install flow-based leak protection systems and strategically place water sensors under appliances and pipes. | Learn more about leak protection systems, including how to qualify for a premium credit: Leak Protection |
| Flood & Sewer Backup Prevention | Use sump pumps, direct water away from the foundation, and consider sewer-backup prevention devices. | See Preventing Water Damage |
| Roof Hardening & Storm Preparation | Reinforce roofs with impact-resistant materials and clean gutters and downspouts to improve water flow. | Learn more about maintaining your roof. |
| Security Enhancements | Improve exterior lighting, secure locks, clear sightlines, and use biometrics or smart cameras. | Watch Smart Security Strategies for Chapter Houses webinar. |
| Self-Inspection & Preventive Maintenance | Complete MJ Sorority’s Chapter House Self-Inspection form at least annually—summer is an ideal time. | Download MJ’s Chapter House Self-Inspection Form. |
| Emergency Readiness | Prepare an emergency response plan and keep updated inventories and documentation of property and valuables. | Review emergency resources at MJ Sorority. |
Beyond Bricks and Mortar
Risk hardening isn’t just about upgraded building materials—it’s about thoughtful planning and clear communication:
- Emergency Response Plan: Train volunteers and collegiate leaders on evacuation, communication, and critical contacts. This resource can help.
- Documentation Management: Keep photos, floor plans, insurance records, and inventory lists backed up securely. Check out our House Corporation Inventory Checklist to help.
- Regular Walkthroughs: Use the self-inspection form and monthly to-do lists to spot small issues before they grow.
The Bottom Line for House Corporation Volunteers
Being proactive is more than a best practice—it’s a duty of care. Your role is to steward the property for current and future members. Strengthening the chapter house today not only limits financial loss—it fosters a safer, more secure environment for your members and your organization.
As always, contact us with any questions.
As the academic year winds down, this month’s newsletter is packed with practical tips to help your chapter close out the year safely and smoothly. This month’s newsletter is focused on setting the stage for a smooth and safe break—and a strong start to the next academic year.
- Skip to the housing section where this month you’ll find tips for deep cleaning and mold prevention over the summer
- Click straight through to the chapter services section for guidance for reviewing officer transitions and answers to common questions about alumnae use of the facility.
Summer often brings quieter campuses—but it also brings an uptick in severe weather risks. From torrential rain and flash flooding to high winds, hurricanes, and even tornadoes, the summer season can cause serious property damage, particularly when chapter houses are unoccupied or unmonitored.
While you can’t prevent storms, you can reduce their impact by preparing the facility in advance. Here are five smart steps house corporations and property managers can take now to protect the chapter house during the summer months.
1. Identify and Address Hidden Vulnerabilities
Storm damage is often worsened by small maintenance issues that have gone unnoticed. Roof leaks, cracked foundations, blocked drainage, or worn seals around doors and windows can all become big problems when severe weather hits.
Before the height of summer storm season, walk the property or coordinate a professional inspection. Focus on known weak spots—roof seams, basement entries, foundation cracks, and aging drainage systems. Clear gutters and downspouts to ensure water flows away from the house, not toward it. Fixing these issues now can help avoid emergency repairs and insurance claims later.
Applicable MJ resources to help:
2. Establish a Local Emergency Contact
With the chapter members away during the summer, having someone nearby who can respond quickly is essential. Designate a local point of contact—such as a House Director, House Corporation volunteer, chapter advisor, or trusted contractor—who can monitor severe weather alerts and physically check the house following a storm.
This person can assess damage early, prevent additional losses (such as water intrusion), and coordinate immediate repairs. Even something as simple as tarping a roof or boarding a window can make a major difference in preventing further damage.
Applicable MJ resources:
3. Don’t Underestimate Flood Risk
Flooding isn’t just a coastal or river-adjacent risk—it can happen anywhere, especially when sudden storms overwhelm local drainage systems. Older homes or those with basements are particularly vulnerable.
Evaluate your property’s risk and consider steps such as:
- Sealing basement walls and windows.
- Installing or testing sump pumps, ideally with battery backups.
- Relocating key items—like mechanical systems or stored furnishings—above ground level.
- Maintaining relationships with local contractors and remediation vendors so help is readily available if needed.
Read more about increasingly severe storms and how best to prepare. Learn more about leak detection technology to help minimize water damage.
4. Prepare for Wind Damage Before It Happens
High winds from summer storms can be incredibly destructive. They can tear off shingles, topple trees, and turn outdoor furniture into airborne hazards.
Help reduce your risk by:
- Inspecting and repairing roofing and flashing.
- Trimming tree limbs that hang over the building or utility lines.
- Securing or storing outdoor furniture, signage, or trash bins.
- Reinforcing vulnerable exterior elements, such as entry doors or older windows, especially if the house is located in a hurricane or tornado-prone area.
Applicable MJ resources to learn more:
5. Emergency Planning Isn’t Optional—It’s Essential
Having a documented emergency response plan is a crucial part of risk management, but a plan that’s never shared or practiced won’t be much help in the middle of a storm. House Corporations should take time each year to review and update their storm and emergency procedures. Make sure everyone involved—house directors, local volunteers, advisors, and key vendors—knows their role before a crisis occurs.
Think through the key questions:
- Who monitors local weather alerts and determines when action is needed?
- Who checks the property after a storm or initiates emergency repairs?
- What’s the communication plan between the House Corporation, volunteers, and headquarters?
- Do all relevant parties have access to important documents, contact lists, MJ claims contact, and vendor information if power or internet is down?
Even if the house is unoccupied, a clear response protocol helps minimize damage, speeds up repairs, and keeps everyone informed and prepared.Bottom of Form
Advance Planning Makes a Big Difference
With the chapter house unoccupied, it’s easy for minor issues to go unnoticed until they become major problems. Taking time now to prepare for summer weather can protect the property and reduce your to-do list come fall move-in. If you’re unsure where to start, your MJ Sorority team is always here to support you.
A special edition newsletter from MJ Sorority to help you make the most of the summer season.
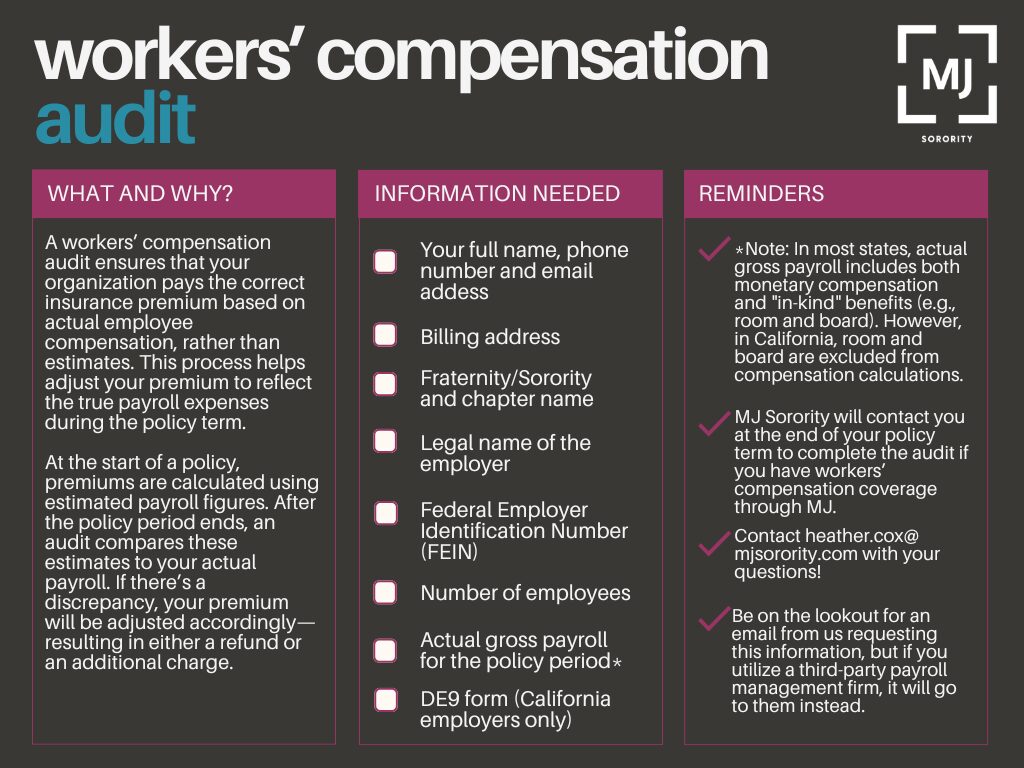
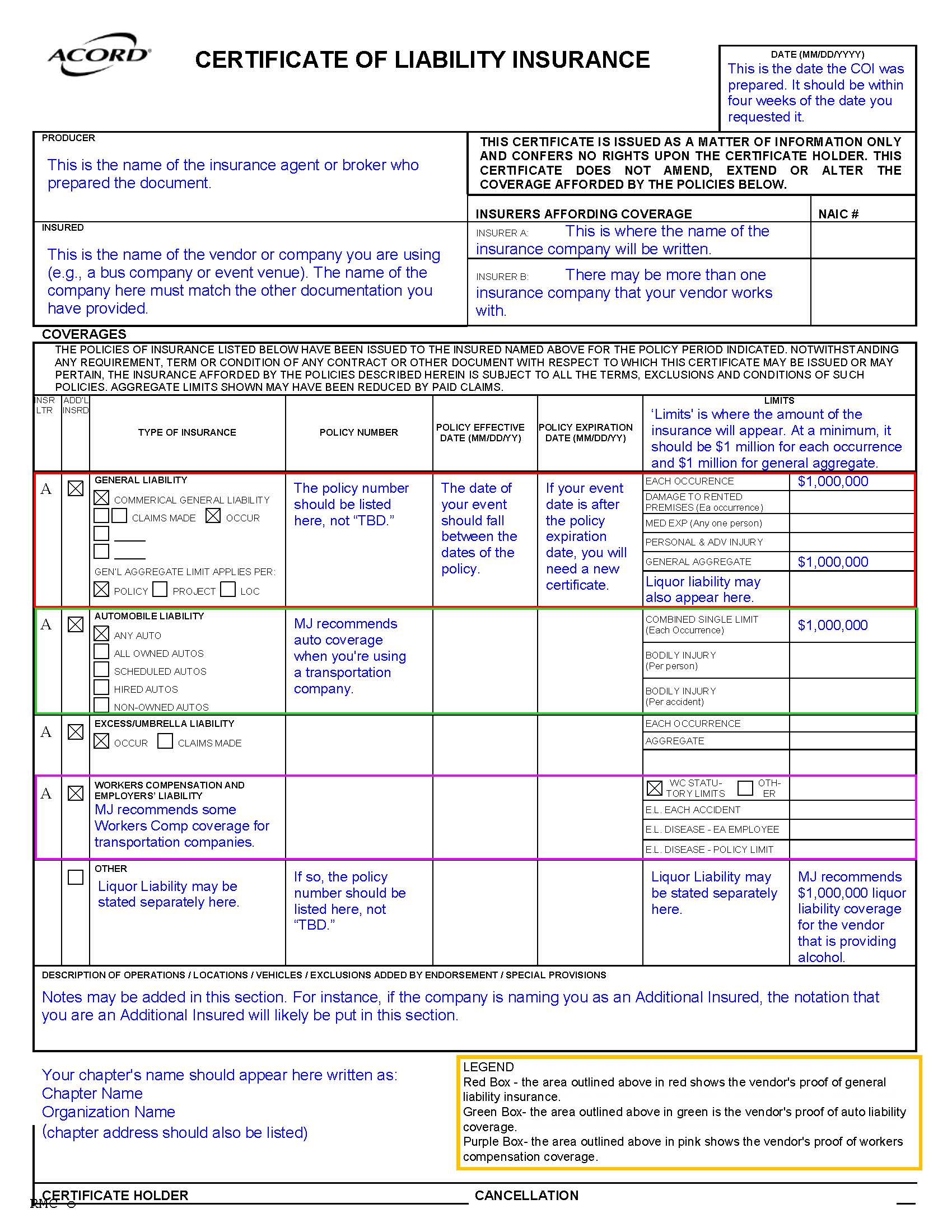
When you’re hosting an event at a venue or other third-party location, your organization’s guidelines require that you obtain proof of insurance from that venue. This is done through a certificate of insurance. A certificate of insurance (COI) is a document that shows a business has insurance coverage. The venue may very well also request to see your organization’s COI, which you can request here (remember you need to have a written request from the venue, often found in your contract!). And be sure to obtain a venue’s COI before signing a contract with the venue for your event.
A certificate of insurance is an official document that summarizes an organization’s insurance coverage. It is the only acceptable form of this confirmation and is part of your due diligence in vetting the venue for an event. Sometimes venues offer declarations sheets or other parts of their policy as proof of insurance. This is not the same as a certificate and should not be accepted.
So you’ve gotten a venue’s certificate of insurance—now what? Certificates of insurance include a wide variety of information, some of which is important, and some of which isn’t relevant to your review. When you receive a certificate, the following are items you should absolutely look for:
Who is the named insured? The named insured should be the name of the vendor. Sometimes this may be a different name “doing business as” the “name of the venue”. For example, if you’re hosting an event at ABC Event Center, the venue’s COI may have the named insured listed as “XYZ Corporation, doing business as ABC Event Center”.
What are the policy limits? MJ recommends that third parties hold the following minimum limits of liability insurance:
| General Liability ($1,000,000 per occurrence) | Liquor Liability ($1,000000 per occurrence) | Automobile Liability ($1,000,000 per occurrence) | Workers’ Compensation ($500,000 per accident) |
| Any third party contractor should hold this amount of general liability coverage | This is recommended if the third party vendor is serving alcohol at a chapter event | This is recommended for third parties providing transportation, such as a bus company | We recommend this coverage for any contractors you engage with |
If a third-party does not hold these minimum limits, please contact your headquarters to determine whether you need to identify an alternative option. There may be some exceptions and differentiations in your organization’s event guidelines.
Liquor liability in particular can be tricky as sometimes it’s listed separately and sometimes is included in the general liability coverage. If it’s included under the general liability section, liquor liability coverage will be noted specifically and you should be able to easily deduce that there is adequate coverage.
What are the policy effective dates? The effective dates are typically one year in length and should cover the date(s) of your event. If the policy is for a short period of time or do not cover the date(s) of your event, the certificate does not provide proof of coverage for your event and you should reach back out to the venue to get clarification and another certificate that provides proof of adequate coverage for your event.
Is your organization listed as a certificate holder? Being a certificate holder means you’re receiving a (COI) to verify that the policyholder has adequate insurance coverage. You are not covered by the policy and don’t have any rights under it. While this may not be required by your organization, it confirms that you have received an up-to-date policy pulled specifically at your request.
Most certificates are relatively straightforward, however, there are some things to look out for that may be problematic:
- Be sure text hasn’t been superimposed on an existing certificate. This is fraudulent and should not be accepted.
- Be sure that the certificate is complete and matches the information in your contract with the venue (i.e. address, name, etc.)
- DO NOT accept COIs that list effective dates as covering one day or a very short period of time. These policies are not acceptable and will not provide adequate coverage in the event of a claim and typically exclude sororities. If you have questions about a policy term, please contact your headquarters
Obtaining a COI is a vital risk management practice when planning events and is a lifelong skill! When hiring a contractor to work on your home or hosting a wedding or baby shower for a friend, you will again run into certificate review.
Click here for a sample COI with our recommendations.
Introduction
Partnering with other student organizations to co-host social or philanthropic events is a common and valued part of campus life. However, these co-sponsored events increase your chapter’s liability—and potentially that of your national organization—beyond what you’d face by simply attending an event as a guest.
As a co-sponsor of an event, your chapter’s liability, or duty of care, is elevated. Because of this elevated liability, it is crucial you engage in good risk management to ensure your event is safe for attendees. This responsibility should not be delegated to the other co-sponsoring organization and you must be an active participant in this important part of hosting an event.
Managing Risk as a Co-Sponsor
Good risk management starts at the beginning of the event planning process. If you are not going to be part of planning the event, you should never agree to co-sponsor. Don’t bring this increased liability to your chapter if you are not going to have an influence on the event and its focus on being safe. There have been cases where chapters were held liable for injuries at events they didn’t help organize, simply because they agreed to co-sponsor. These have resulted in serious and expensive legal claims—a reminder that putting your chapter’s name on an event carries real responsibility.
Before agreeing to co-sponsor, make sure the partnering organization is adequately insured. Just as you would require proof of insurance from a venue, the same should apply to your co-sponsor. If the other organization lacks adequate coverage at acceptable limits of liability, your chapter could be left to shoulder most of the financial burden in the event of a claim.
Where a co-sponsor or third party, such as a venue, is not insured or inadequately insured, it will likely fall on the sorority to cover most of the costs of the claim(s). In the history of the sorority insurance program, we have had several situations where a co-sponsoring organization, such as a men’s fraternity, did not have sufficient limits, and the sorority policy was forced to pay more for the claim than their negligence equated to in the incident.
Spotlight on Co-Sponsoring Events with Men’s Fraternities
In many cases, the other co-sponsor is a men’s fraternity and the co-sponsored event is held on the men’s fraternity’s property. As owners of the property, they are in a much better position to control potentially risky exposures, such as egress from a building, proper lighting of the exterior, etc. Liability follows control and as the owner of the property their liability should be greater than that of a guest to the property, like the co-sponsoring sorority. All the more reason why the men’s fraternity should have sufficient limits of insurance.
Conclusion
Co-sponsored events can be successful and safe, but only when all parties take risk management seriously and are properly insured. If those conditions aren’t met, the event should not move forward.
Officer transitions are a pivotal time for any sorority chapter. A well-executed transition maintains stability and preserves institutional knowledge. Without proper planning, chapters risk losing valuable experience and insight. We are noticing how important it is for chapter officers and advisors to help train their replacements to ensure continuity, especially in the area of event planning.
No matter what time of year your officers are transitioning, here are some tips to make officer transitions seamless and effective:
1. Start Early
Transitions shouldn’t begin when new officers are elected—they should be an ongoing process. Encourage outgoing officers to document their roles and responsibilities throughout their term so new leaders don’t have to start from scratch.
2. Create a Comprehensive Officer Manual
Each position should have a detailed manual outlining key duties, deadlines, and best practices. This can include:
- Contact lists for campus administrators, advisors, and other key contacts
- Budget templates and financial records
- Event planning timelines and risk management protocols
- Past successes and lessons learned
- Important websites and resources
- Be sure to check with your national headquarters for officer manual templates
3. Hold One-on-One Training Sessions
Outgoing officers should meet individually with their successors to provide hands-on training. Walking through daily tasks, software tools, and decision-making processes helps new officers feel more prepared. We are also available to develop and deliver risk management education for officers during larger officer transition periods. Contact Kit Moorman, Director of Risk Management Education, for more information.
4. Conduct a Full Executive Board Transition Meeting
A group meeting with both outgoing and incoming executive boards fosters collaboration and alignment on chapter goals. This is also a great time to discuss upcoming initiatives, potential challenges, and strategic plans for the year ahead.
5. Leverage Mentorship from Alumnae and Advisors
Advisors and alumnae can provide continuity by offering historical context and best practices. Encourage new officers to maintain open communication with these key resources.
6. Utilize Digital Storage for Important Documents
A shared, organized digital archive (such as Google Drive or a chapter management platform) ensures critical documents are easily accessible and not lost between transitions.
7. Encourage Reflection and Feedback
Ask outgoing officers to share what worked well and what could be improved. Creating an open dialogue allows new leaders to learn from past experiences and refine their approach.
By prioritizing a structured transition process, chapters can ensure their new officers step into their roles with confidence, armed with the knowledge and resources they need to succeed. A strong transition plan not only preserves the chapter’s legacy but also sets the foundation for future success.
Just click the printer icon to download a printable version for your use.
Kitchen & Common Areas
- Deep clean inside and behind appliances (fridge, oven, microwave)
- Sanitize sink, garbage disposal, and drains
- Steam clean carpets and upholstery
- Dust and clean ceiling fans, vents, and baseboards
- Empty and disinfect trash cans and recycling bins
- Wash window screens and sills
Bathrooms
- Scrub tile, grout, and shower walls
- Clean under and behind toilets and sinks
- Check for signs of leaks or moisture around plumbing
- Ensure exhaust fans are functional and clean
Bedrooms & Storage
- Inspect closets for musty smells or signs of moisture
- Vacuum under beds and behind furniture
- Check window areas for condensation or mold
- Leave closet doors cracked open to improve airflow
Basement & Utility Areas
- Inspect for signs of standing water or leaks
- Run dehumidifiers as needed
- Clean AC drip pans and check filters
- Ensure gutters and downspouts direct water away from the foundation
General Mold Prevention
- Keep HVAC running (set to auto with temp ~78–80°F)
- Place moisture absorbers in closets or bathrooms
- Schedule at least one mid-summer walkthrough
- Review maintenance logs and check for unresolved plumbing issues
Even with protections put in place by internal IT departments or outside partners, email remains an unsecured and unreliable technology capable of being hacked, altered and manipulated. Read this report by our partners at CHUBB outlining some of the most prominent tactics that bad actors are using in their social engineering schemes. Included are examples of the most common schemes and the best ways to prevent them.
When chapter members request to bring an emotional support animal (ESA) with them to their chapter house, there is a unique set of challenges presented to the housing corporation: how to review requests, create and communicate clear guidelines for housing the animal, the impact on other members, and more.
While we have seen organizations take several different approaches to managing this process, one thing is true across organizations: housing corporations should be clear and consistent when creating and enforcing emotional support animal policies. Because of the legal requirements of the Emotional Support Animal Request process, it is important that you engage your national organization to help you navigate the process and ensure consistency from chapter to chapter of your organization. There are a few basic laws and policies that should be considered when creating your own procedure, which we outline below.
The Fair Housing Act (FHA) & Emotional Support Animals (ESAs)
The Fair Housing Act prohibits discrimination in renting, buying, or financing housing. In general, the FHA protects people with disabilities and requires housing providers to make reasonable accommodations for persons with disabilities. An ESA can be a reasonable accommodation, but can also be unreasonable. It is essential that an organization create and codify procedures to review ESA requests fairly and consistently across properties.
What’s Required in an ESA Approval Process
As stated above, it is crucial that your organization is clear and consistent when creating and enforcing an ESA policy. Some key points to consider are:
- Notification Requirements;
- A person with a disability must notify their housing provider if they need a reasonable accommodation and the provider must grant the request if it is reasonable, as a part of an interactive process between the resident and the property owner.
- Connection between ESA and Disability; and
- The ESA must provide a service to the person with a disability that is connected to that person’s disability.
- Whether a Reasonable Accommodation can be made.
- A reasonable accommodation is a change or adjustment made to a housing policy or practice that allows a person with a disability to equally use and enjoy their dwelling.
- Some accommodations can be unreasonable, and all requests should be subject to the same analysis.
Creating an ESA Approval Process
Housing corporations should be clear and consistent when creating and enforcing emotional support animal policies. The easiest way to accomplish this is to analyze requests at the national level and provide consistent guidance to local house corporations that may need to manage their own property’s requests.
Requests should be reviewed by a committee and be clearly outlined in the organization’s procedures. It’s also crucial to engage the member making the request throughout the review process. Members’ needs, paperwork, and circumstances can vary greatly. Ensuring that your process is navigable and reasonable will protect you from the consequences of a “take it or leave it” approach.
Once a request is reviewed, be sure to communicate a plan to the member. This should outline any reasonable accommodations being made or unreasonable accommodation requests that are being denied. If there are expectations of the member, such as keeping a dog on a leash, they should also be outlined and formally acknowledged by the member.
Common Pitfalls
Look out for common mistakes and misconceptions about ESA policies:
- A request for a reasonable accommodation can be made at any time.
- An organization cannot require a specific notification form so long as the required information is provided in writing.
- While housing providers can request information to evaluate a person’s disability and related need, they are not entitled to know an individual’s diagnosis. It is appropriate for the housing provider to require documentation from the person’s health care professional that affirms a disability is present and that the ESA provides for the need related to that disability.
- The need to fill the house does not qualify as an undue burden and does not make a request unreasonable. To deem a request unreasonable, some other circumstance(s) must be present.
- An ESA policy cannot limit the size or breed of an ESA. However, it is permissible to deny a request because of specific issues with an animal’s conduct.
Making reasonable accommodations for members’ emotional support animals is key in effectively managing a property. By following these guidelines, you’re well equipped to create organization wide policies to consistently review requests and provide reasonable accommodations.
If you have questions about a specific policy or procedure or are looking for further advice, please reach out to your client executive or consult your inter/national headquarters.
This article is based on a presentation by Amy Hebbeler of Fraternal Law Partners, shared with MJ Sorority. With thanks to both Amy and Fraternal Law for sharing.





