With the semester underway, September is a great time to hit pause, reset, and make sure your chapter is starting strong. In honor of Campus Safety Awareness Month, this issue highlights practical steps you can take to keep members safe, protect your property, and strengthen your chapter operations.
Fall is in full swing—and so are chapter events! From homecoming gatherings to formals, now’s the perfect time to double-check that your venues and vendors have the right coverage in place. It’s also a great season to tackle routine fall maintenance around the chapter house, ensuring everything is safe, comfortable, and ready for cooler months ahead.
In this issue of our monthly newsletter, you’ll also find trick-or-treating safety tips to help your chapter host community events responsibly, highlights from our recent CrowdChange webinar on smarter fundraising, and important reminders about preventing slips and falls as the weather turns colder.
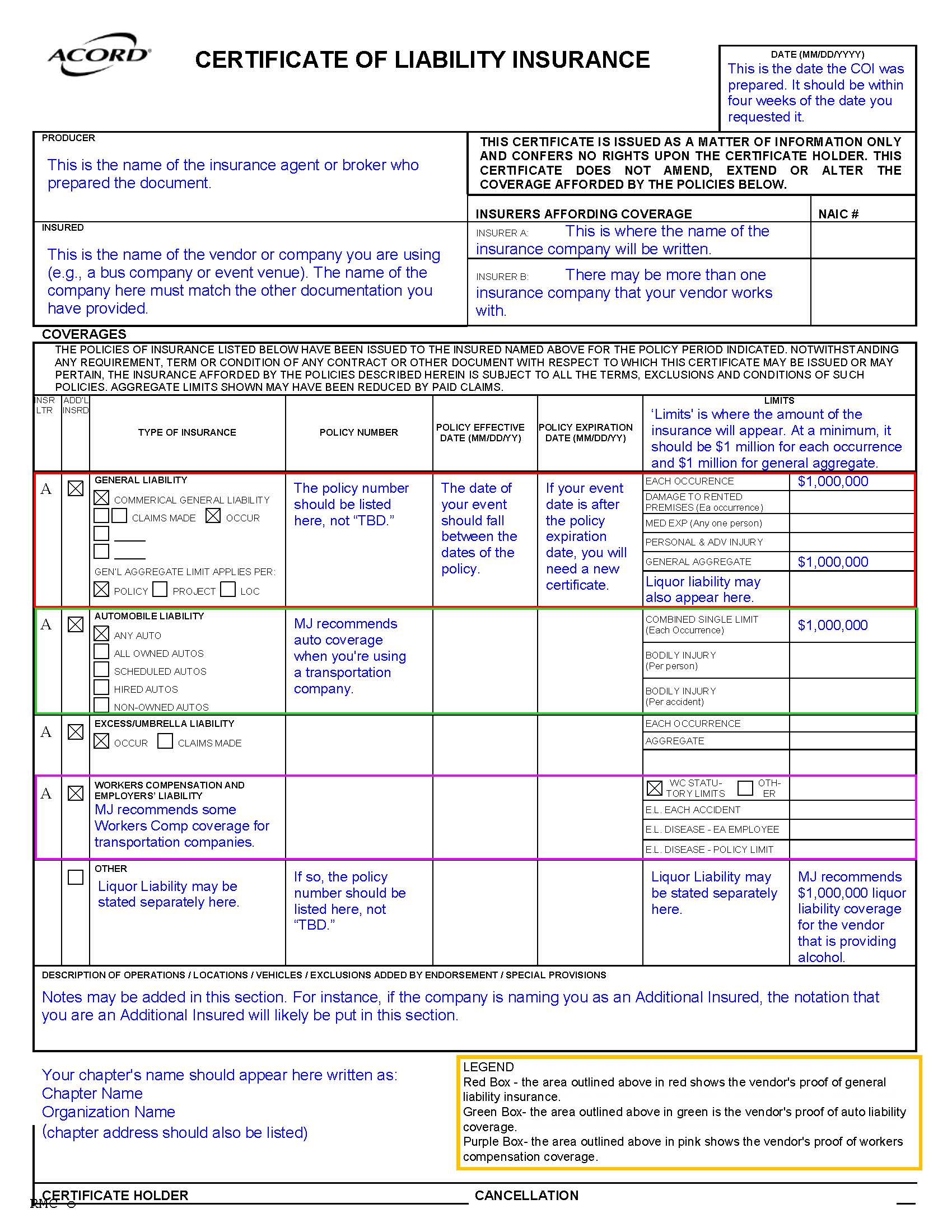
When a venue, vendor, or other third party provides your chapter with a Certificate of Insurance, it can be tough to know what you’re really looking at. To make it easier, we’ve created a sample certificate with MJ’s recommended wording and limits highlighted. Use this guide as a quick reference to spot what’s missing or out of place, so you can feel confident that the coverage being provided truly protects your chapter.
As your members return and the academic year begins, we’ve gathered timely updates to help your chapter and housing operations run smoothly. This month’s highlights include:
- How to safely reopen your chapter house after summer (or any) break
- Why it’s critical to report all wind and hail claims—even minor ones
- Key back-to-school reminder about university certificates of insurance
- Floodplain awareness and your property’s FEMA designation
- A real-world phishing scam close call you’ll want to share
- A fresh nudge to explore Events Central for your fall planning
This month’s newsletter is focused on setting the stage for a smooth and safe break—and a strong start to the next academic year.
- Skip to the housing section where this month you’ll learn more about building resiliency at the chapter house – and why it’s more important than ever.
- Click straight through to the chapter services section for guidance on co-sponsored events
- In this month’s extra section, we teach you more about workers’ compensation audits and the importance of two-factor authentification to protect you from cyber threats.
As the academic year winds down, this month’s newsletter is packed with practical tips to help your chapter close out the year safely and smoothly. This month’s newsletter is focused on setting the stage for a smooth and safe break—and a strong start to the next academic year.
- Skip to the housing section where this month you’ll find tips for deep cleaning and mold prevention over the summer
- Click straight through to the chapter services section for guidance for reviewing officer transitions and answers to common questions about alumnae use of the facility.
When you’re hosting an event at a venue or other third-party location, your organization’s guidelines require that you obtain proof of insurance from that venue. This is done through a certificate of insurance. A certificate of insurance (COI) is a document that shows a business has insurance coverage. The venue may very well also request to see your organization’s COI, which you can request here (remember you need to have a written request from the venue, often found in your contract!). And be sure to obtain a venue’s COI before signing a contract with the venue for your event.
A certificate of insurance is an official document that summarizes an organization’s insurance coverage. It is the only acceptable form of this confirmation and is part of your due diligence in vetting the venue for an event. Sometimes venues offer declarations sheets or other parts of their policy as proof of insurance. This is not the same as a certificate and should not be accepted.
So you’ve gotten a venue’s certificate of insurance—now what? Certificates of insurance include a wide variety of information, some of which is important, and some of which isn’t relevant to your review. When you receive a certificate, the following are items you should absolutely look for:
Who is the named insured? The named insured should be the name of the vendor. Sometimes this may be a different name “doing business as” the “name of the venue”. For example, if you’re hosting an event at ABC Event Center, the venue’s COI may have the named insured listed as “XYZ Corporation, doing business as ABC Event Center”.
What are the policy limits? MJ recommends that third parties hold the following minimum limits of liability insurance:
| General Liability ($1,000,000 per occurrence) | Liquor Liability ($1,000000 per occurrence) | Automobile Liability ($1,000,000 per occurrence) | Workers’ Compensation ($500,000 per accident) |
| Any third party contractor should hold this amount of general liability coverage | This is recommended if the third party vendor is serving alcohol at a chapter event | This is recommended for third parties providing transportation, such as a bus company | We recommend this coverage for any contractors you engage with |
If a third-party does not hold these minimum limits, please contact your headquarters to determine whether you need to identify an alternative option. There may be some exceptions and differentiations in your organization’s event guidelines.
Liquor liability in particular can be tricky as sometimes it’s listed separately and sometimes is included in the general liability coverage. If it’s included under the general liability section, liquor liability coverage will be noted specifically and you should be able to easily deduce that there is adequate coverage.
What are the policy effective dates? The effective dates are typically one year in length and should cover the date(s) of your event. If the policy is for a short period of time or do not cover the date(s) of your event, the certificate does not provide proof of coverage for your event and you should reach back out to the venue to get clarification and another certificate that provides proof of adequate coverage for your event.
Is your organization listed as a certificate holder? Being a certificate holder means you’re receiving a (COI) to verify that the policyholder has adequate insurance coverage. You are not covered by the policy and don’t have any rights under it. While this may not be required by your organization, it confirms that you have received an up-to-date policy pulled specifically at your request.
Most certificates are relatively straightforward, however, there are some things to look out for that may be problematic:
- Be sure text hasn’t been superimposed on an existing certificate. This is fraudulent and should not be accepted.
- Be sure that the certificate is complete and matches the information in your contract with the venue (i.e. address, name, etc.)
- DO NOT accept COIs that list effective dates as covering one day or a very short period of time. These policies are not acceptable and will not provide adequate coverage in the event of a claim and typically exclude sororities. If you have questions about a policy term, please contact your headquarters
Obtaining a COI is a vital risk management practice when planning events and is a lifelong skill! When hiring a contractor to work on your home or hosting a wedding or baby shower for a friend, you will again run into certificate review.
Click here for a sample COI with our recommendations.
Introduction
Partnering with other student organizations to co-host social or philanthropic events is a common and valued part of campus life. However, these co-sponsored events increase your chapter’s liability—and potentially that of your national organization—beyond what you’d face by simply attending an event as a guest.
As a co-sponsor of an event, your chapter’s liability, or duty of care, is elevated. Because of this elevated liability, it is crucial you engage in good risk management to ensure your event is safe for attendees. This responsibility should not be delegated to the other co-sponsoring organization and you must be an active participant in this important part of hosting an event.
Managing Risk as a Co-Sponsor
Good risk management starts at the beginning of the event planning process. If you are not going to be part of planning the event, you should never agree to co-sponsor. Don’t bring this increased liability to your chapter if you are not going to have an influence on the event and its focus on being safe. There have been cases where chapters were held liable for injuries at events they didn’t help organize, simply because they agreed to co-sponsor. These have resulted in serious and expensive legal claims—a reminder that putting your chapter’s name on an event carries real responsibility.
Before agreeing to co-sponsor, make sure the partnering organization is adequately insured. Just as you would require proof of insurance from a venue, the same should apply to your co-sponsor. If the other organization lacks adequate coverage at acceptable limits of liability, your chapter could be left to shoulder most of the financial burden in the event of a claim.
Where a co-sponsor or third party, such as a venue, is not insured or inadequately insured, it will likely fall on the sorority to cover most of the costs of the claim(s). In the history of the sorority insurance program, we have had several situations where a co-sponsoring organization, such as a men’s fraternity, did not have sufficient limits, and the sorority policy was forced to pay more for the claim than their negligence equated to in the incident.
Spotlight on Co-Sponsoring Events with Men’s Fraternities
In many cases, the other co-sponsor is a men’s fraternity and the co-sponsored event is held on the men’s fraternity’s property. As owners of the property, they are in a much better position to control potentially risky exposures, such as egress from a building, proper lighting of the exterior, etc. Liability follows control and as the owner of the property their liability should be greater than that of a guest to the property, like the co-sponsoring sorority. All the more reason why the men’s fraternity should have sufficient limits of insurance.
Conclusion
Co-sponsored events can be successful and safe, but only when all parties take risk management seriously and are properly insured. If those conditions aren’t met, the event should not move forward.
Officer transitions are a pivotal time for any sorority chapter. A well-executed transition maintains stability and preserves institutional knowledge. Without proper planning, chapters risk losing valuable experience and insight. We are noticing how important it is for chapter officers and advisors to help train their replacements to ensure continuity, especially in the area of event planning.
No matter what time of year your officers are transitioning, here are some tips to make officer transitions seamless and effective:
1. Start Early
Transitions shouldn’t begin when new officers are elected—they should be an ongoing process. Encourage outgoing officers to document their roles and responsibilities throughout their term so new leaders don’t have to start from scratch.
2. Create a Comprehensive Officer Manual
Each position should have a detailed manual outlining key duties, deadlines, and best practices. This can include:
- Contact lists for campus administrators, advisors, and other key contacts
- Budget templates and financial records
- Event planning timelines and risk management protocols
- Past successes and lessons learned
- Important websites and resources
- Be sure to check with your national headquarters for officer manual templates
3. Hold One-on-One Training Sessions
Outgoing officers should meet individually with their successors to provide hands-on training. Walking through daily tasks, software tools, and decision-making processes helps new officers feel more prepared. We are also available to develop and deliver risk management education for officers during larger officer transition periods. Contact Kit Moorman, Director of Risk Management Education, for more information.
4. Conduct a Full Executive Board Transition Meeting
A group meeting with both outgoing and incoming executive boards fosters collaboration and alignment on chapter goals. This is also a great time to discuss upcoming initiatives, potential challenges, and strategic plans for the year ahead.
5. Leverage Mentorship from Alumnae and Advisors
Advisors and alumnae can provide continuity by offering historical context and best practices. Encourage new officers to maintain open communication with these key resources.
6. Utilize Digital Storage for Important Documents
A shared, organized digital archive (such as Google Drive or a chapter management platform) ensures critical documents are easily accessible and not lost between transitions.
7. Encourage Reflection and Feedback
Ask outgoing officers to share what worked well and what could be improved. Creating an open dialogue allows new leaders to learn from past experiences and refine their approach.
By prioritizing a structured transition process, chapters can ensure their new officers step into their roles with confidence, armed with the knowledge and resources they need to succeed. A strong transition plan not only preserves the chapter’s legacy but also sets the foundation for future success.
Spring is in full bloom with the April edition of MJ Sorority’s News & Notes, filled with fresh perspectives on sorority housing and membership to help you manage risk and plan for the season ahead!
Here’s what you don’t want to miss in this month’s newsletter:
- Skip to the housing section where this month we’re advising you on what to do in the event of roof damage
- Click straight through to the chapter services section for a discussion of the nuances of Emotional Support Animal (ESA) requests in chapter houses
- Or jump to our cyber section this month sharing an important resource on social engineering.
Check out the whole thing!
Welcome spring with the March edition of MJ Sorority’s News & Notes, filled with fresh insights to help you manage risk and plan for the season ahead!
Here’s what else you don’t want to miss in this month’s newsletter:
- Skip to the housing section where this month we’re helping you prepare for the season ahead, including storm readiness and the importance of roof inspections.
- Click straight through to the chapter services section for transportation best practices to keep members safe during events.
- And more!





